Coding with success: project realization & production checklist
Explore practical advice on bringing a software project to fruition and access a free checklist for deploying applications into production.

The next version of your custom software is ready! But there’s one important step missing…deployment!
Deployment is a crucial stage in the life cycle of an IT project.
In our guide to custom software deployment, we’ll explore the definition of software deployment, as well as the three main categories of deployment that exist. And since deployment is not risk-free, we’ll look at the 9 potential risks associated with this operation.
Deployment refers to the process of integrating lines of code written by developers (i.e. compiled files) into the production server in order to make a new feature or module available, or to correct a bug or technical debt.
A “hot fix” is a bug correction applied to software in production. This term is often used for fixes that are urgent and necessary to resolve critical problems affecting operations or security.
The characteristics of a hot fix are :
A “fix”, or patch, is a modification made to software to resolve a bug or operating problem. Unlike a hot fix, a fix is generally less urgent and can follow the normal development cycle, including testing phases before being deployed. It has the following characteristics:
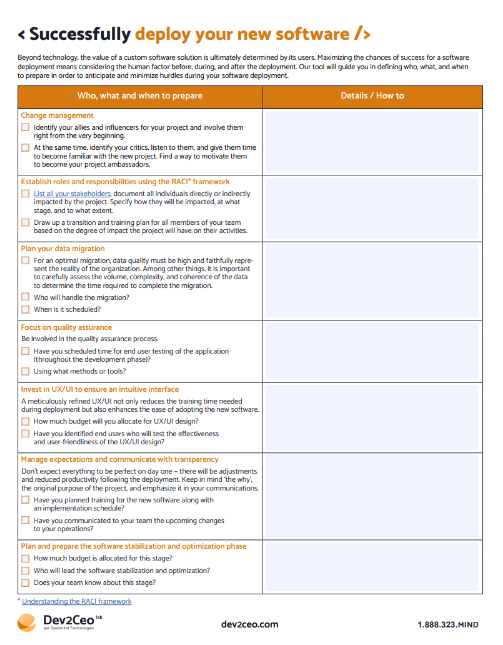
Explore practical advice on bringing a software project to fruition and access a free checklist for deploying applications into production.

Feature deployment refers to the introduction of new features or capabilities into software. This can include adding new features, modifying existing ones, or improving software performance.
It has 3 characteristics:
1. Technical failures and bugs
(Frequency: High, Impact: Variable)
Compatibility problems, bugs not detected during testing, or coding errors may cause the application to malfunction.
This risk concerns technical faults in the software, such as bugs not detected during testing, compatibility problems between different parts of the software or with third-party systems, or coding errors. These faults can lead to application malfunctions, ranging from minor to critical, and require patches or updates to resolve.
2. Safety issues
(Frequency: Medium, Impact: High)
Security vulnerabilities may be introduced, threatening data protection and application integrity.
This risk is about security vulnerabilities introduced during software deployment, which may compromise data confidentiality, integrity or availability. Security vulnerabilities can be exploited by malicious individuals to gain access to sensitive information or compromise the application’s proper functioning.
3. Unexpected traffic loads
(Frequency: Medium, Impact: Medium to High)
Unexpected increases in traffic can overload servers.
Unexpected increases in traffic can overload servers and underlying infrastructures, resulting in slowdowns, downtime or poor application performance. This overload may be due to a sudden spike in usage, DDoS (distributed denial of service) attacks or other unforeseen factors.
4. Non-compliance with User Requirements
(Frequency: Medium, Impact: Medium)
Functionality may not fully meet end-users’ needs or expectations.
This problem may be due to a misunderstanding of user requirements, faulty implementation or changes in user needs that were not taken into account during software development. (read our article on the 6 causes of cost overruns in software development)
5. Integration problems
(Frequency: Medium, Impact: Medium)
Difficulties integrating new functionality with existing application components or with third-party systems.
This risk concerns difficulties in integrating the new functionality with existing application components or with third-party systems. Integration problems can lead to compatibility conflicts, operating errors or unexpected application behavior.
6. Performance degradation
(Frequency: Medium, Impact: Medium)
New functionality may adversely affect overall application performance.
The addition of new functionalities can sometimes lead to a degradation in overall application performance, such as longer loading times, slower user interfaces or increased consumption of system resources. This degradation can affect the user experience and diminish user satisfaction.
Subscribe to receive our exclusive updates directly to your email.

7. Regression
(Frequency: Medium, Impact: Medium to High)
New bugs or problems may appear in features that previously worked correctly.
Regression occurs when new bugs or problems appear in features that previously worked correctly. This may be due to changes or updates in the source code, conflicts between different parts of the software, or regressions not detected during testing.
8. Compatibility problems
(Frequency: Medium, Impact: Medium)
Incompatibility with certain browsers, devices or operating systems.
This risk concerns the incompatibility of the application with certain browsers, devices or operating systems. Compatibility issues may result in a poor user experience, limited functionality or display errors on certain platforms, which may reduce the accessibility and usefulness of the application for some users.
9. User resistance to change
(Frequency: Low, Impact: Medium)
Users may be reluctant or slow to adopt new functionality.
Users can sometimes be reluctant or slow to adopt new features or changes in the application. This may be due to established habits, an aversion to change, or a distrust of new technologies. Resistance to change can slow down the adoption of new functionality and limit its overall effectiveness.
In conclusion, we’ve explored the three main categories of deployment: hot fixes, fixes and feature deployments, highlighting the essential differences between each.
However, it’s crucial to recognize that deployment is not without risk.
We have identified nine potential risks, ranging from technical faults and security issues to integration challenges and user resistance to change. These risks underline the importance of careful planning, rigorous testing and effective communication with stakeholders throughout the deployment process.
Ultimately, a strategic and proactive approach is required to mitigate these risks and ensure a successful deployment. By integrating best practices in project management, software development and IT security, teams can maximize the chances of a successful deployment, guaranteeing user satisfaction and optimal performance of the bespoke software.
One major factor to consider is the scope of the application during development. As highlighted in our article on “The 3 Main Risks of Fixing the Scope of an Application During Development”, locking in the scope too early can lead to inflexibility, increased costs, and a higher likelihood of delays. These risks are not just theoretical—they directly affect the deployment phase. If the scope has been rigidly fixed, any necessary changes discovered during deployment can be costly and complex to implement, potentially compromising the success of the entire project.
Tell us more about your needs so that we can better route your project to our specific SWAT team.
1
During the brainstorming phase, we work with you to identify potential solutions to your business challenges to generate the technology response that aligns with your business objectives.
2
Through our requirements gathering process, we work closely with you to define and prioritize your needs, ensuring that our solutions are tailored to meet your specific requirements.
3
This phase marks the beginning of our partnership. We’ll finalize the project plan and establish clear communication channels to ensure a smooth and successful project execution.